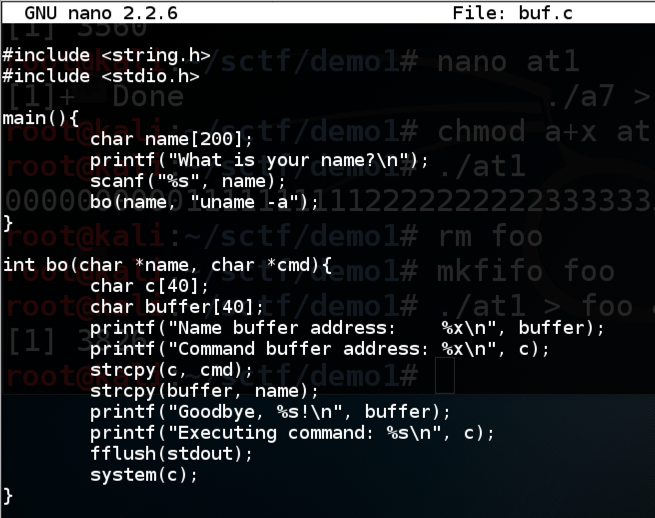
Simple Buffer Overflow
Explanation
The form below calls a C program with a simple buffer overflow
vulnerability. The "name" variable can overflow into the
"cmd" variable.
Here's the source code:
Vulnerable Form
Try putting in a short name, and then make the name longer until you get
unexpected results.
For a good time, try this string:
0123456789012345678901234567890123456789ls
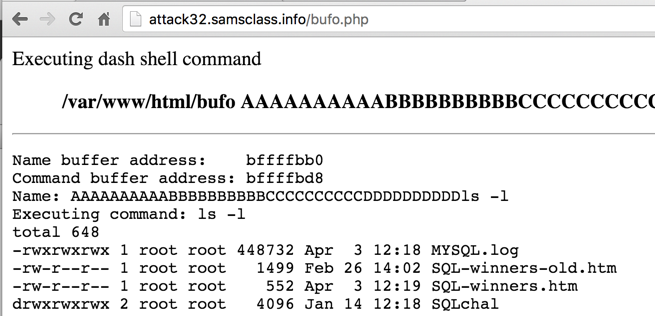
Challenge 1: Long List
Execute the "ls -l" command by entering
a crafted name,
so it shows file details,
as shown below.
Hint
If spaces are annoying you, try
this.
|
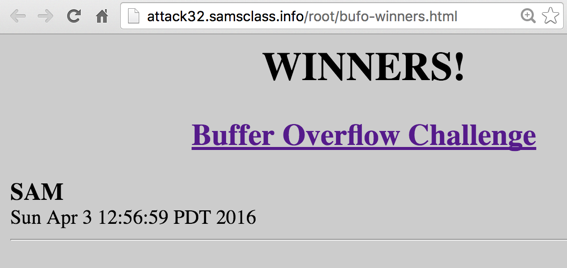
Challenge 2: Add Your Name to the Hall of Fame
Put your name in this file:
/tmp/bufo/winners
After one minute, your name will appear
on the WINNERS page here:
http://attack32.samsclass.info/root/bufo-winners.html
Hint
To open a dash shell, execute this command in a Linux or OS X Terminal:
dash
Now you can practice the commands to create the files
you need to.
|
Source code and explanation
Sources
I based this on the "pwn1" and "pwn2"
challenges in the
2015
SCTF competition.
Posted 4-3-16 by Sam Bowne
Last modified 6-28-16



